NIST Framework Components
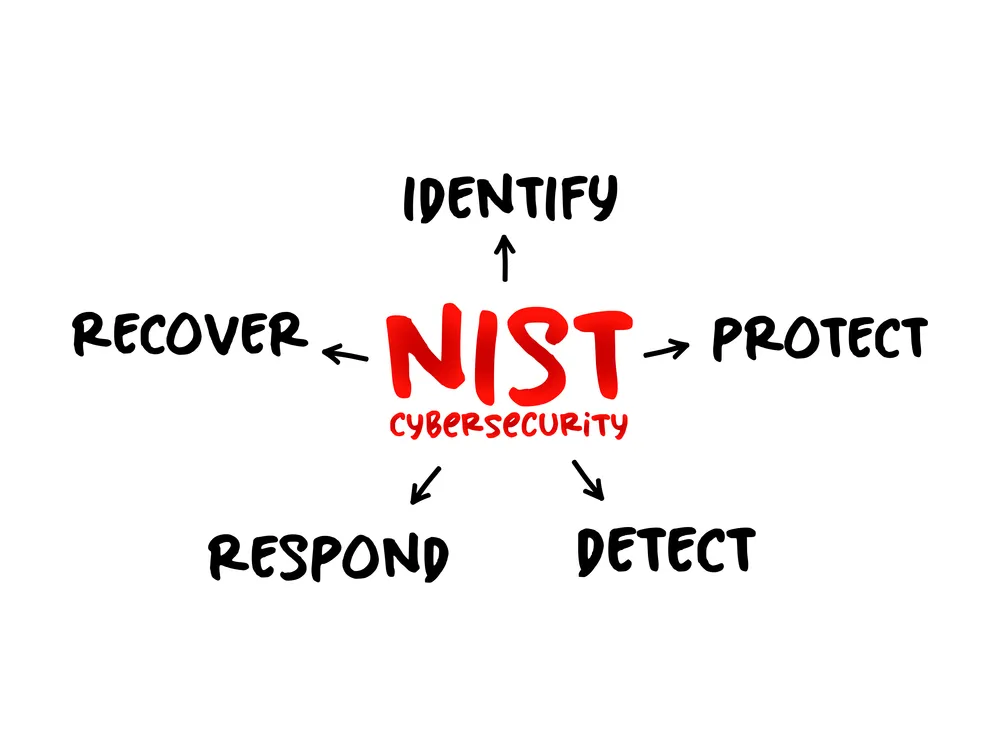
The core NIST Cybersecurity Framework structures vulnerability management activities around five essential functions that provide comprehensive coverage of cybersecurity operations. These functions include Identify (creating organizational understanding to manage risk), Protect (implementing safeguards to deter attacks), Detect (developing plans for identifying cybersecurity events), Respond (establishing incident response procedures), and Recover (maintaining strategies for system restoration and resilience).
Within this framework, organizations utilize 23 categories and 108 subcategories that break down cybersecurity objectives into granular, outcome-based statements. The framework’s flexibility allows organizations to create both current and target profiles, mapping their existing cybersecurity status against desired future states while adapting the guidelines to their unique business operations and mission requirements.
Six-Phase Management Process
The systematic approach involves six distinct phases that guide organizations through comprehensive vulnerability handling. The process begins with Identification, where vulnerabilities are discovered through scanning tools and threat intelligence platforms, followed by Assessment to determine severity using risk-based scoring systems like CVSS. Mitigation focuses on reducing risks through security patches and configuration updates, while Remediation involves fully addressing vulnerabilities by replacing or updating vulnerable components.
The final phases ensure long-term effectiveness through Verification, which conducts follow-up scans to confirm successful fixes and maintains detailed documentation for audit purposes, and Continuous Monitoring, which uses automated tools for real-time detection of new vulnerabilities and emerging threats. This cyclical process ensures organizations maintain ongoing visibility into their security posture while systematically addressing both existing and newly discovered weaknesses across their entire attack surface.
Implementation Best Practices
Successful implementation requires establishing a comprehensive vulnerability management policy that defines clear roles, responsibilities, and processes for identifying and addressing security weaknesses. Organizations should begin by conducting a thorough asset inventory to identify all IT assets, including servers, endpoints, and cloud environments, ensuring complete visibility across their attack surface.
Automation plays a crucial role in streamlining vulnerability management processes, including configuration management, change management, asset management, and incident response. Regular vulnerability scanning should be combined with risk-based prioritization to address high-severity vulnerabilities first, followed by prompt deployment of vendor-recommended patches and updates. Organizations must also verify fixes through follow-up scans, maintain detailed documentation of vulnerabilities and remediation steps, and implement continuous monitoring using automated tools to detect new threats in real-time.
Business Benefits and Compliance
Organizations implementing NIST-aligned vulnerability management programs experience significant operational and regulatory advantages that extend beyond basic security improvements. Proactive risk mitigation enables detection of vulnerabilities before attackers can exploit them, while compliance assurance helps meet regulatory requirements including HIPAA, PCI-DSS, and federal cybersecurity mandates. The structured approach reduces the overall attack surface by systematically limiting entry points for cybercriminals and ensures business continuity by avoiding costly disruptions from cyber incidents.
The framework facilitates knowledge sharing between organizations, allowing them to benefit from collective experiences and strengthen their security posture through industry best practices. Maintaining detailed vulnerability records ensures audit readiness for compliance and certification processes, while the risk-based prioritization approach enables more effective resource allocation compared to traditional quantity-focused methods. This strategic shift from compliance-driven to risk-based vulnerability management allows organizations to evolve from an infrastructure-focused approach to addressing their entire attack surface systematically.

